It is understandable that most people associate the entirety of the dark web with “The Onion Router” (Tor), as it is unequivocally the most utilized dark net in the world. Most of those who traverse the dark web are likely using Tor, whether it be via Tor Browser itself or a virtual private network (VPN) that offers “over onion” routing. Since its inception in 1995, the Tor network has massively expanded from a military project to the proverbial household name when it comes to what many believe is a “hidden internet.” For us in law enforcement, when it comes to investigating nefarious activities from narcotics trafficking to malware to child pornography, it is extremely likely that the suspect is utilizing Tor in some fashion. It is important to understand the fundamentals of onion routing and how the Tor network functions, and to break the stigmas that we in law enforcement harbor concerning what the “dark web” is.
The Tor Project is a 501(c)(3) research nonprofit based in Massachusetts. It maintains the Tor network en masse and is constantly updating Tor Browser. It is important to understand that the Tor Project wants you to utilize Tor Browser to traverse the Tor network, and most of the security features to maintain the anonymity of the end user are built into Tor Browser. “Onion routing” is the concept of layered protection, much like how an onion has many layers. While onion routing of internet traffic in and of itself is not exclusive to the Tor network (LokiNet offers Oxen onion routing, for example), the Tor network is built upon the Tor circuit, which consists of the Entry (guard), Middle and Exit nodes. The circuit is also constantly changing with each connection, to ensure not only the best browsing experience, but also that no relay node would be consistently connecting based on a user’s geolocation.
“Onion routing” is the concept of layered protection, much like how an onion has many layers.
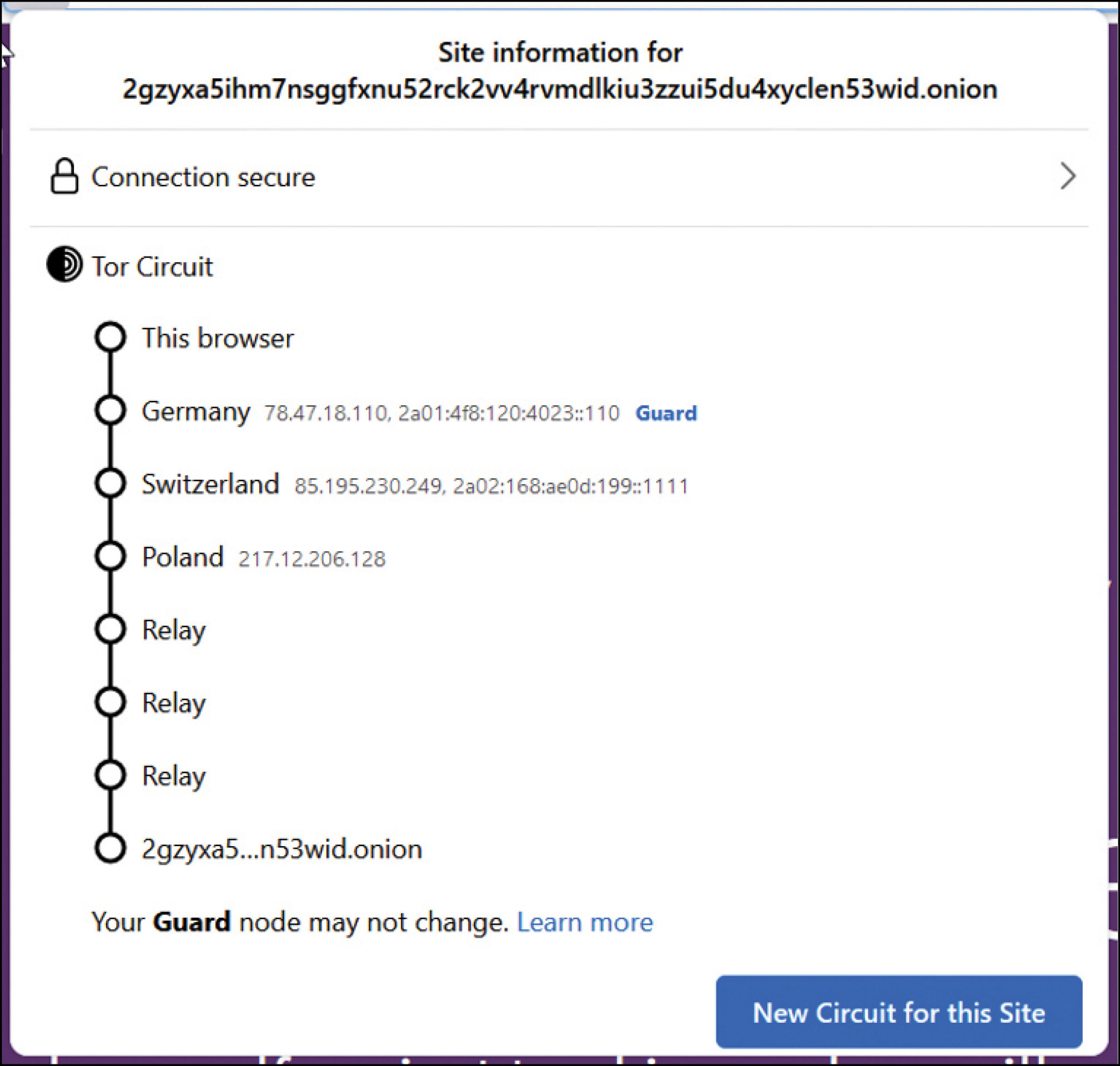
When connecting to the Tor network, whether through Tor Browser or a Tor in-proxy (VPN “over onion” routing), it encodes and encrypts the users’ traffic to the Tor standard. This is what allows the user to visit .onion top-layer domains, which are exclusive to the Tor network (think of these like .com, .net or .gov domains, but exclusive to Tor). Onion sites, also called “hidden services,” are only accessible via the Tor network. They are 56 alphanumeric characters and will always end in d.onion. For example, Tor Project’s .onion domain is http://2gzyxa5ihm7nsggfxnu52rck2vv4rvmdlkiu3zzui5du4xyclen53wid.onion/index.html.
It is important to note that onion sites to do not use Transport Layer Security (TLS)/Secure Sockets Layer (SSL) encryption in the Hypertext Transfer Protocol (HTTP). The encryption process is different on Tor traffic versus the Hypertext Transfer Protocol Secure (HTTPS) TLS/SSL of standard web traffic. This one of the reasons why the Tor Project is constantly updating both the Tor network and Tor Browser, to ensure the encryption of network traffic as well as safety of the Tor Browser usership. Onion sites will also have their own circuit of relay nodes before connecting with the end user’s Exit Node.
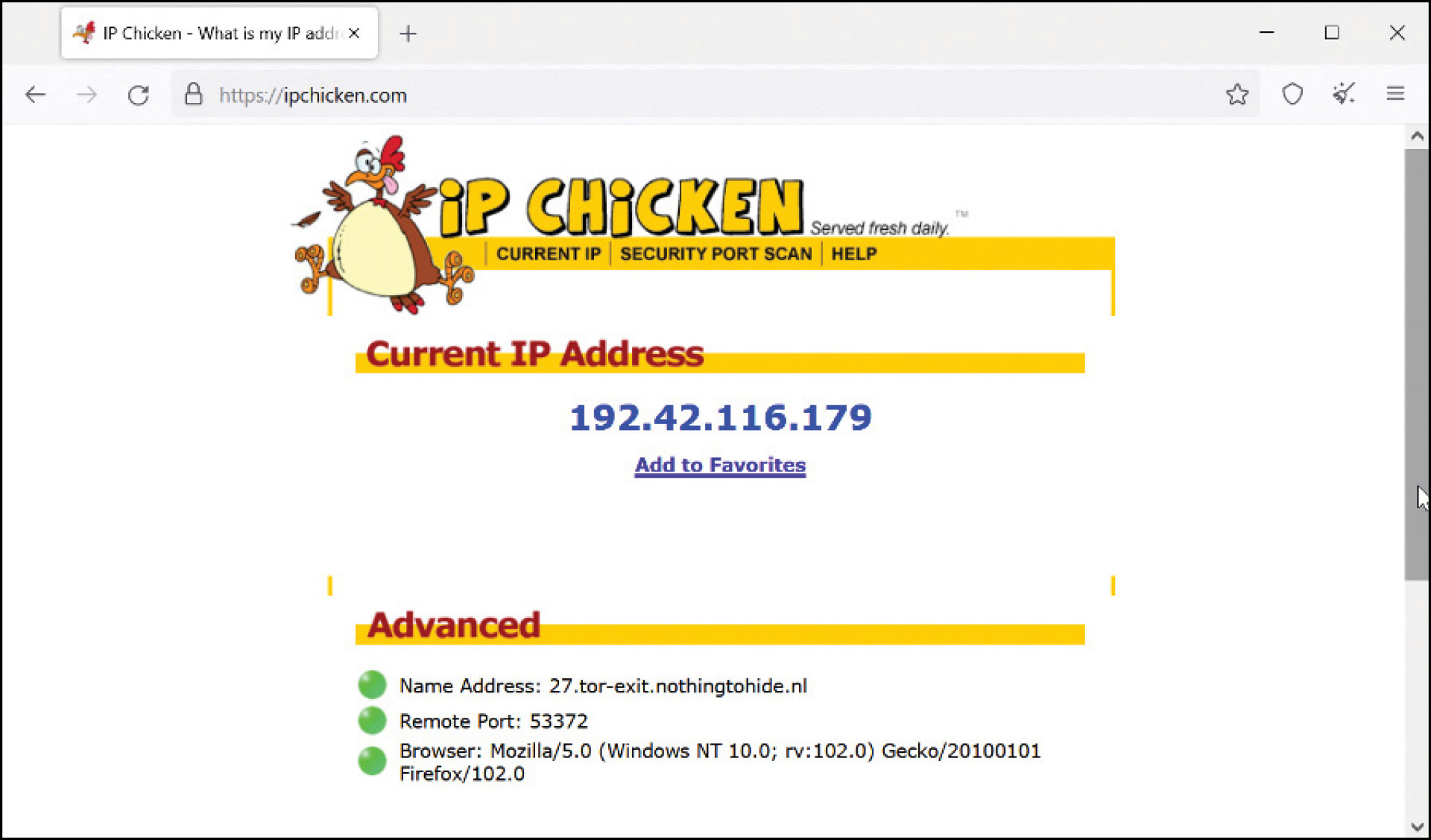
If you are confused or feel there has been too much “computer jargon” for your comfort, that is understandable. In layperson’s terms: Think of the Tor dark net as a small network within the World Wide Web. If we take a closer look at the IP addresses associated with my captured Tor circuit, we can see that Tor relays are commonly observed on the World Wide Web. From the Tor Project’s own words: “Tor is an international software project to anonymize Internet traffic by encrypting packets and sending them through a series of hops before they reach their destination.”
The Tor network could not exist without the internet you might be using right now to read this article (whether on your phone or computer!). This is often a concept that is lost on those who think of the dark web as a separate internet from the one they commonly use.
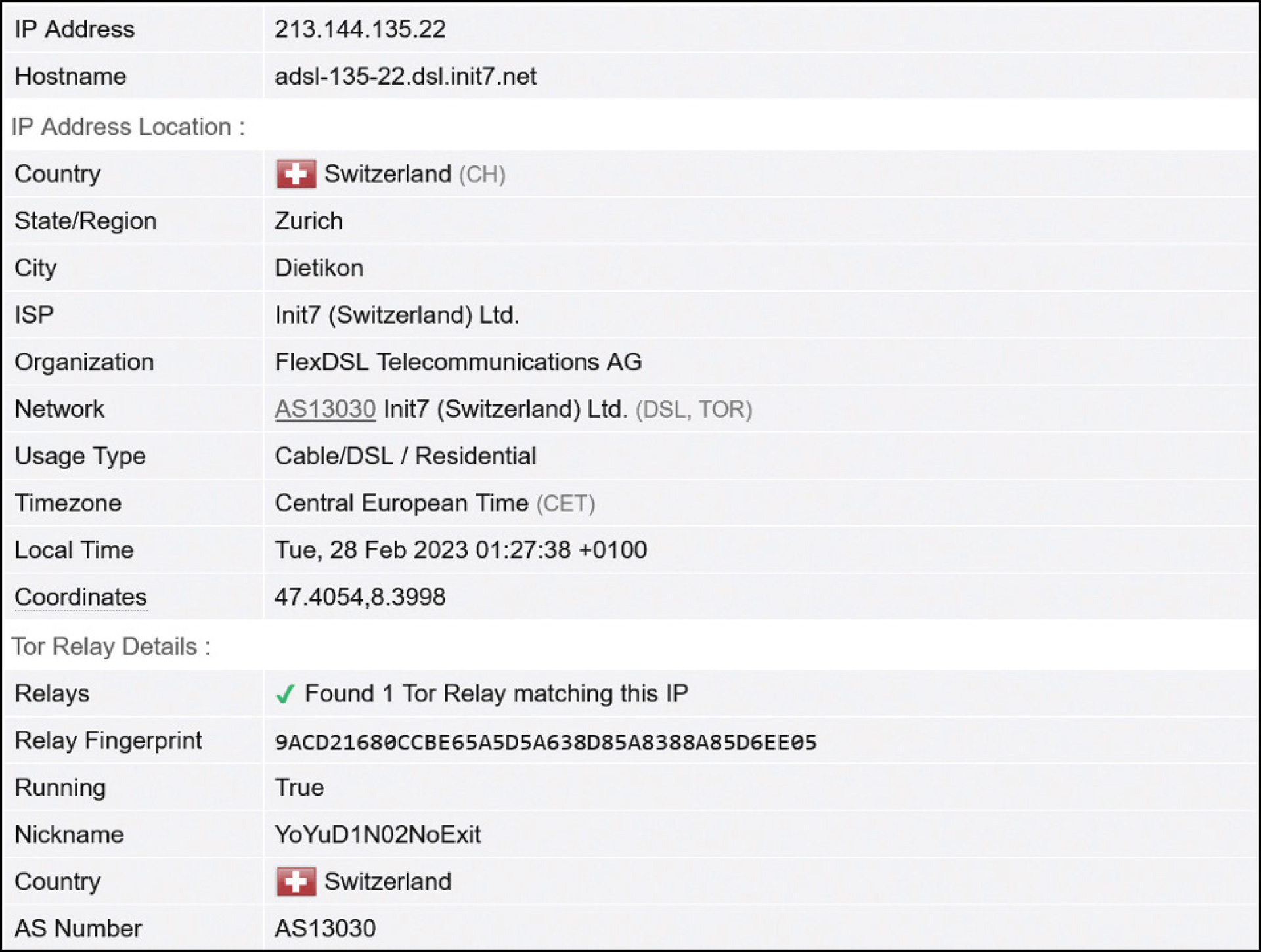
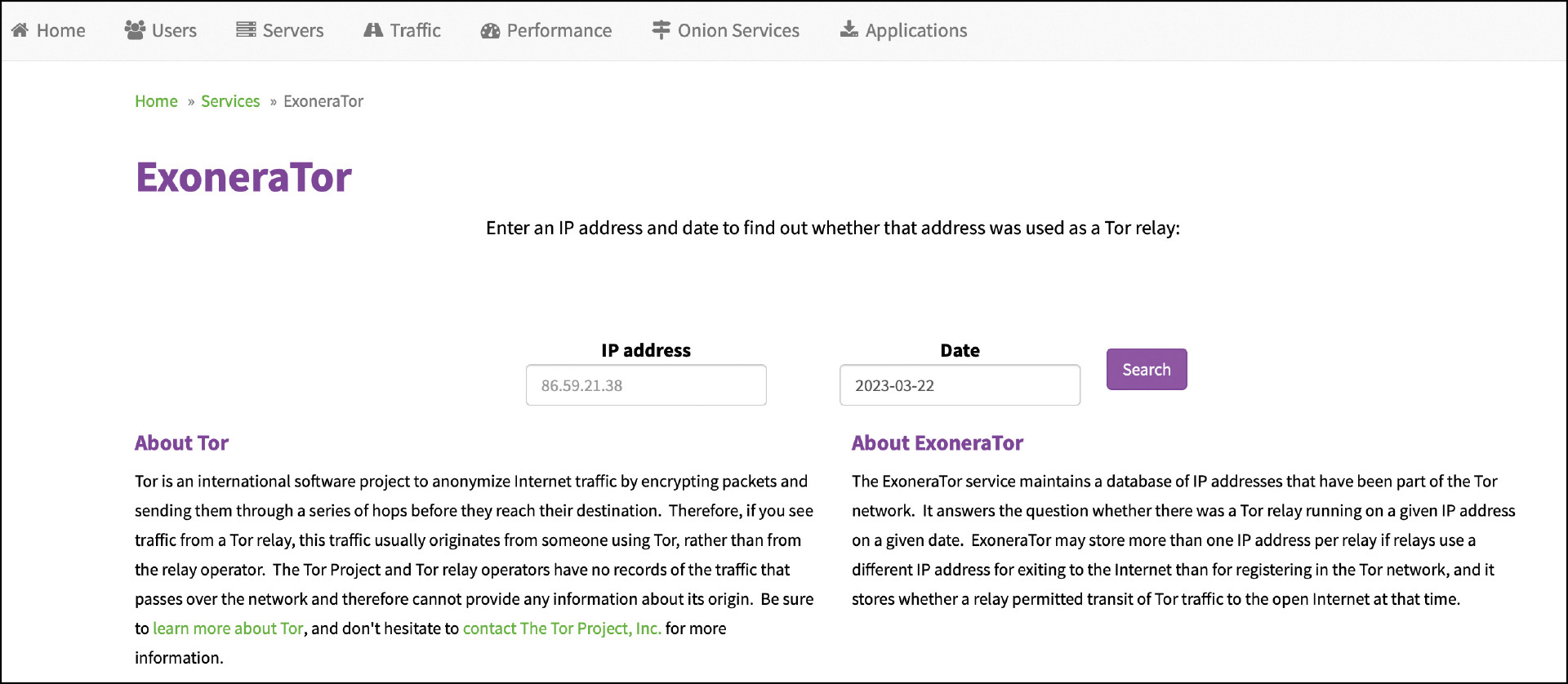
On average, there are close to 2.5 million users of the Tor network each day, whether that’s through Tor Browser or another in-proxy. The Tor Project maintains Tor Metrics (https://metrics.torproject.org), where you can view not only end users of Tor, but also the volume of unique V3 onion domains (an estimated 800,000 as of February 2023) active on the Tor network. Tor Metrics also is home to the ExoneraTor service (metrics.torproject.org/exonerator.html), which can let you know if a specific IP address was in fact being used as a relay node on a specific date if it has not already been recognized as one!
Something to be cognizant of: Usage of the dark web as a whole has increased 300% since 2017 (tinyurl.com/59wk6tzm). In 2020, at the height of the COVID pandemic, usage of the different dark nets also spiked (tinyurl.com/2p9hdebj). The dark web has become ingrained in our internet-centric culture. Despite the prevalent image of the dark web being associated with all things negative and criminal, at its altruistic core it is about internet freedom. The Tor Project is constantly updating both the network and browser to mitigate internet censorship. Because of this, Facebook and the New York Times have their own .onion domains geared toward Tor users.
Working in concert with the Tor Project, the Open Observatory of Network Interference (OONI) measures internet censorship with the free software OONI Probe (ooni.org/install) and publishes its findings in both reports and the OONI Explorer (explorer.ooni.org), a repository for internet service providers worldwide.
I feel it is imperative to understand that, while we in law enforcement often deal with the worst of society, we should not always be equating the use of a dark net like Tor to something criminal. Those who migrate to America from countries that heavily censor the internet for their citizens may be accustomed to utilizing Tor just to go on Facebook or read the news their government doesn’t want them seeing. With the stability and safety of the Tor network, popular VPN providers like Proton and Nord have incorporated “over onion” routing options for their users. When using Tor Browser, the internet traffic is encapsulated within the browser itself versus all the outgoing traffic on your device. When utilizing a VPN with “over onion” routing, it routs all of your outgoing traffic into the Tor network. As such, whatever browser you utilize for normal internet usage (e.g., Chrome, Firefox) can be used to visit .onion domains (pretty cool!).
While there are many sites that host links to the notorious “dark net markets” like the Silk Road that we will always associate with the Tor browser — DarkNetLive (darknetlive.com), DarkNetOne (darknetone.com), Tor.taxi, etc. — I highly encourage you to visit sites like DarkUrl (https://darkurl.site) or Ahmia (ahmia.fi) for the organic Google-like search experience. If you are interested, the web capture tool Hunchly (hunch.ly) offers its Hunchly Daily Dark Web Report (hunch.ly/darkweb-osint), which emails you daily reports of newly observed onion sites and statistics (really cool!). If you want to take your investigations into Tor further, CyberSixgill (cybersixgill.com) has been on the forefront of dark web intelligence and offers an investigative platform for searching across indexed Tor services. Another source that offers a plethora of information and support on not only the Tor dark net but the dark web as a whole is the Anti Human Trafficking Intelligence Initiative (followmoneyfightslavery.org/darkweb-intelligence).
I feel that the dark web is very much a “living thing” and constantly evolving, with the Tor Project being on the forefront of that change. When I first became involved with dark web investigations, if you had told me that in 2023 Tor Browser would be fully compatible with Android phones and available for download on Google Play, I would’ve thought you were crazy. Conversely, if you don’t believe that today kids as young as 13 know how to use Tor Browser on their phones just as much as TikTok or Instagram … you’re now the crazy one.
As seen in the April 2023 issue of American Police Beat magazine.
Don’t miss out on another issue today! Click below:






