I would be remiss if I didn’t acknowledge that the law enforcement community’s perception of the “dark web” has remained uncomfortably stagnant over the past decade. As I have previously written about in American Police Beat — see “Your guide to the alternate ‘dark nets’” in 2022 — the “dark web” is composed of various compartmentalized “darknets.” The advent of blockchain technology and subsequent implementation of blockchain DNS (domain name service) has caused a paradigm shift for the internet en masse, putting us on the precipice of what is commonly dubbed “Web3.” While the traditional darknets like TOR, I2P and Hyphanet (Freenet) maintain their loyal usership and unmatched popularity, peer-to-peer darknets have found their way from a being niche interest to widespread adoption.
The difference between peer-to-peer darknets and “traditional” darknets is rooted in how the internet traffic enters and traverses the darknet. TOR, for example, implements “onion routing,” consisting of the TOR circuit. I2P, on the other hand, implements “tunneling” or something colloquially known as “garlic routing.” To traverse any of the sites hosted on these “traditional” darknets, the internet traffic must adhere to the prescribed protocol and also requires software to be utilized by the end user to satisfy those requirements. Said software can be a specific internet browser (like the TOR Browser), an executable file or an operating system configuration. Peer-to-peer darknets, on the other hand, operate with much more portability.
Peer-to-peer darknets merely require access via a peer for entry. For example, Telegram’s The Open Network (TON) requires a user to configure their internet browser to access the TON proxies in order to visit TON domains (URLs that end in .ton). Without accessing proxies, visiting the TON domains would not be possible. Revisiting the “traditional” darknet connectivity comparison, it is important for readers to comprehend that your traffic inbound to a peer is completely visible, meaning you are visible to the darknet. This is drastically different from the “traditional” darknets that obfuscate a user’s identity before connection to the darknet. With peer-to-peer darknets, only once you are connected to a peer can your traffic become anonymized and conflated with the other users’ traffic.

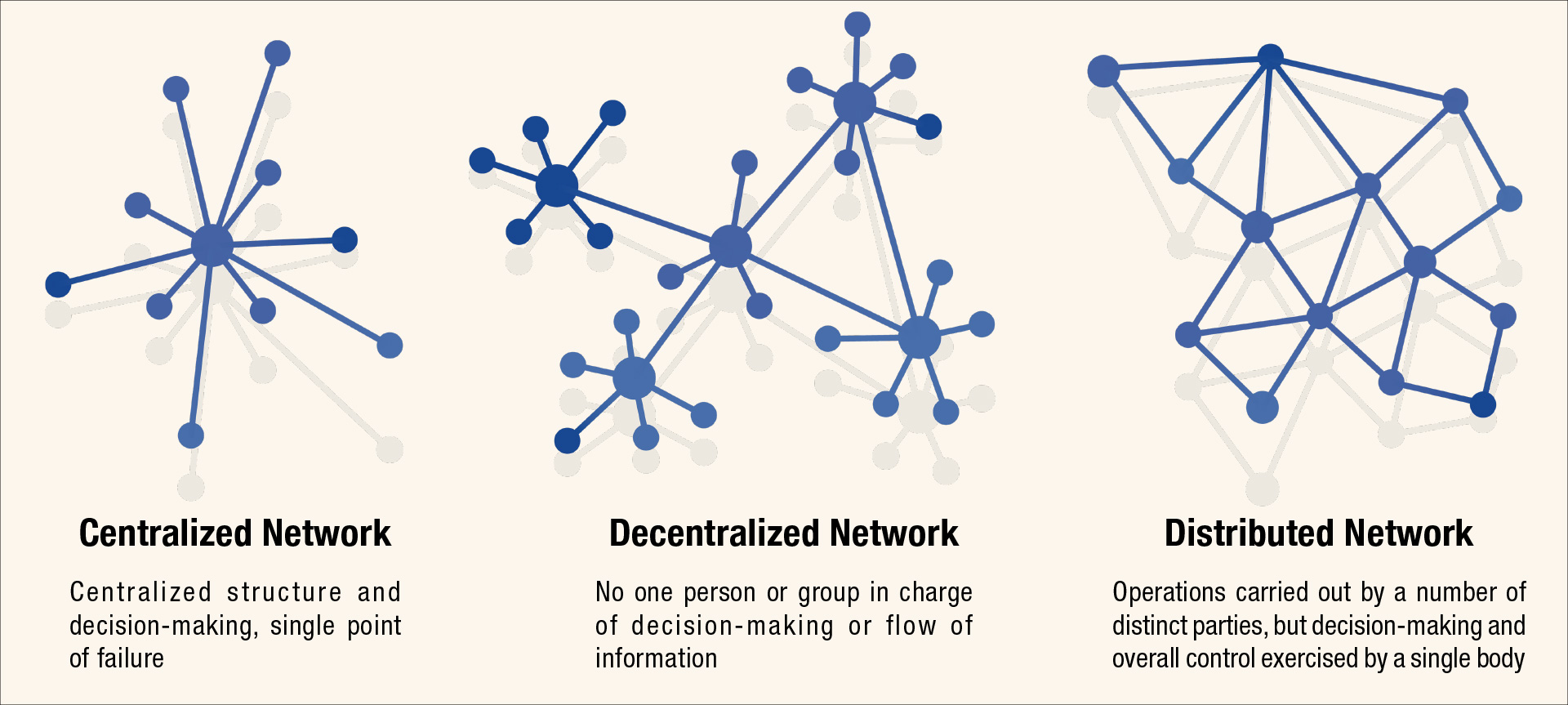
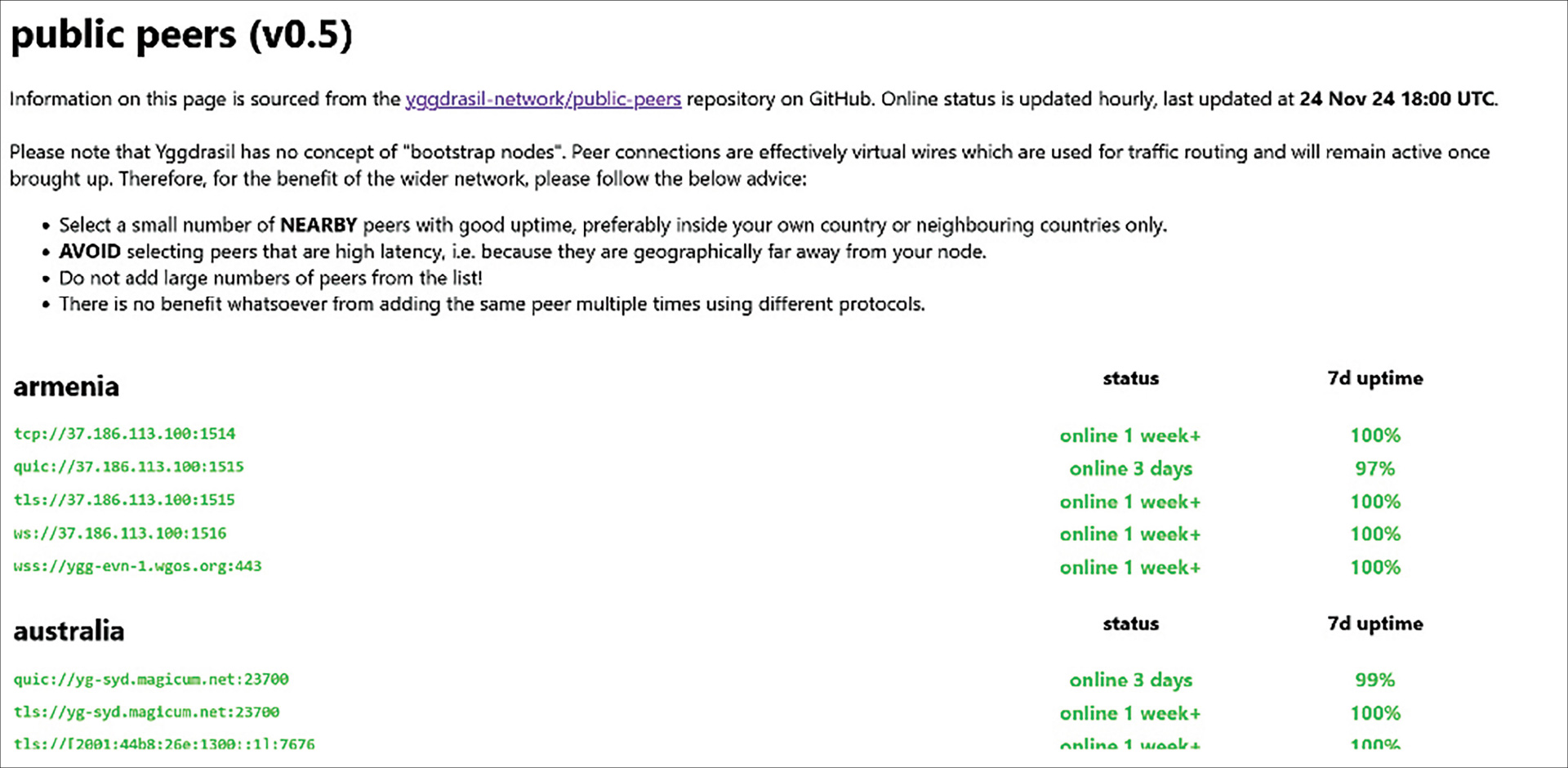
One such peer-to-peer darknet to highlight is Yggdrasil. What makes Yggdrasil most interesting is that shares a software component, similar to the “traditional” darknets like TOR and I2P; however, it simply allows for the routing of traffic into the Yggdrasil network, and the user must select their peer. As with all peer-to-peer darknets, the peers have to be visible and maintained in some sort of centralized repository.
Peer-to-peer darknets are not browser-specific, unlike the TOR browser, which is built upon the Mozilla Firefox framework. You can use whichever browser you prefer; e.g., Chrome, Firefox, Edge, etc. Pertaining to Yggdrasil configuration specifically, the software router is merely allowing your internet traffic to connect to one of the network’s peers via one of your internet’s 65,500-plus available ports. Your traffic is not obfuscated, meaning the peer can see your true IP address as you enter. To reiterate, once connection with a peer has been established, only then can the peer-to-peer darknet sites be traversed.
It is not lost on me that, to the law enforcement community, everything I have just covered may seem nebulous or abstract. And that is certainly OK! You do not have to be an “expert” in this space in order to be able to investigate suspects utilizing peer-to-peer darknet services. But it is also imperative for even the lay reader to understand that the internet as we know it is changing, and that while peer-to-peer darknets may be a smaller fiefdom of the internet, the advent of decentralized and distributed networks is already here.
For further reading on peer-to-peer darknets, and well as the possibilities of the decentralized and distributed web, I highly encourage you to visit such projects as Urbit (urbit.org), TON (ton.org), Tribler (github.com/Tribler/tribler) and Agregore (agregore.mauve.moe). In my humble opinion, these networks are the future of what we in law enforcement colloquially refer to as the “dark web,” and I believe we will see the aforementioned “traditional” darknets gravitating their infrastructure toward the distributed/decentralized network overlays. With privacy as well as anonymity remaining paramount concerns for the internet experience today, it is only natural that services like peer-to-peer darknets offer an alternative to what we all know as the “dark web.”
As seen in the January 2025 issue of American Police Beat magazine.
Don’t miss out on another issue today! Click below:






